Comprehensive SOC as a Service with Sttor
Protect Your Infrastructure with Our Expert SOC Solutions
About Our SOC as a Service
At Sttor, we provide robust SOC solutions tailored to your organization's needs. Our SOC as a Service helps you safeguard your infrastructure with real-time monitoring, threat detection, and incident response.
- Enhanced security and threat detection
- Compliance with industry standards
- 24/7 monitoring and incident response
- Integration with existing tools and systems
One product, unlimited solutions

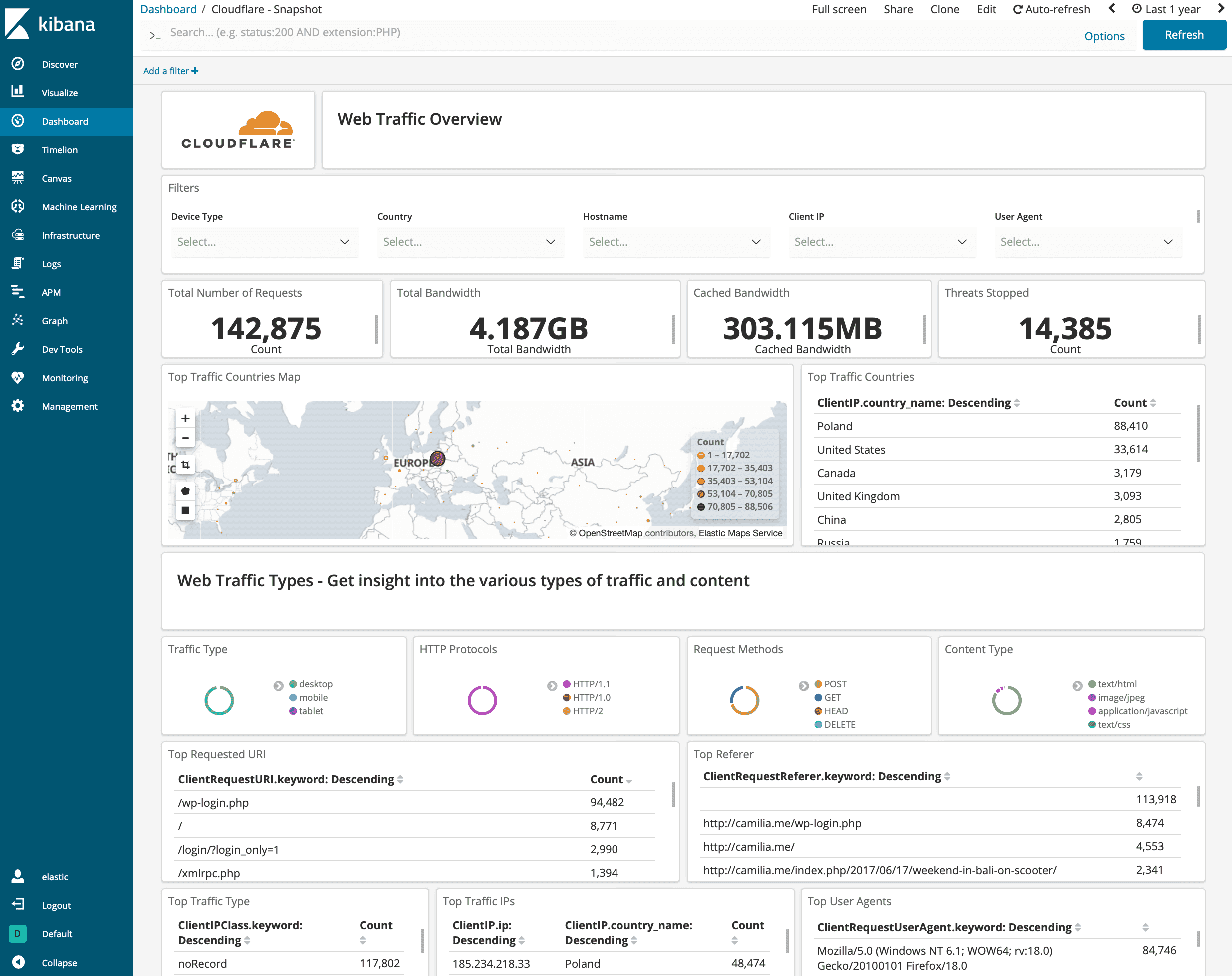
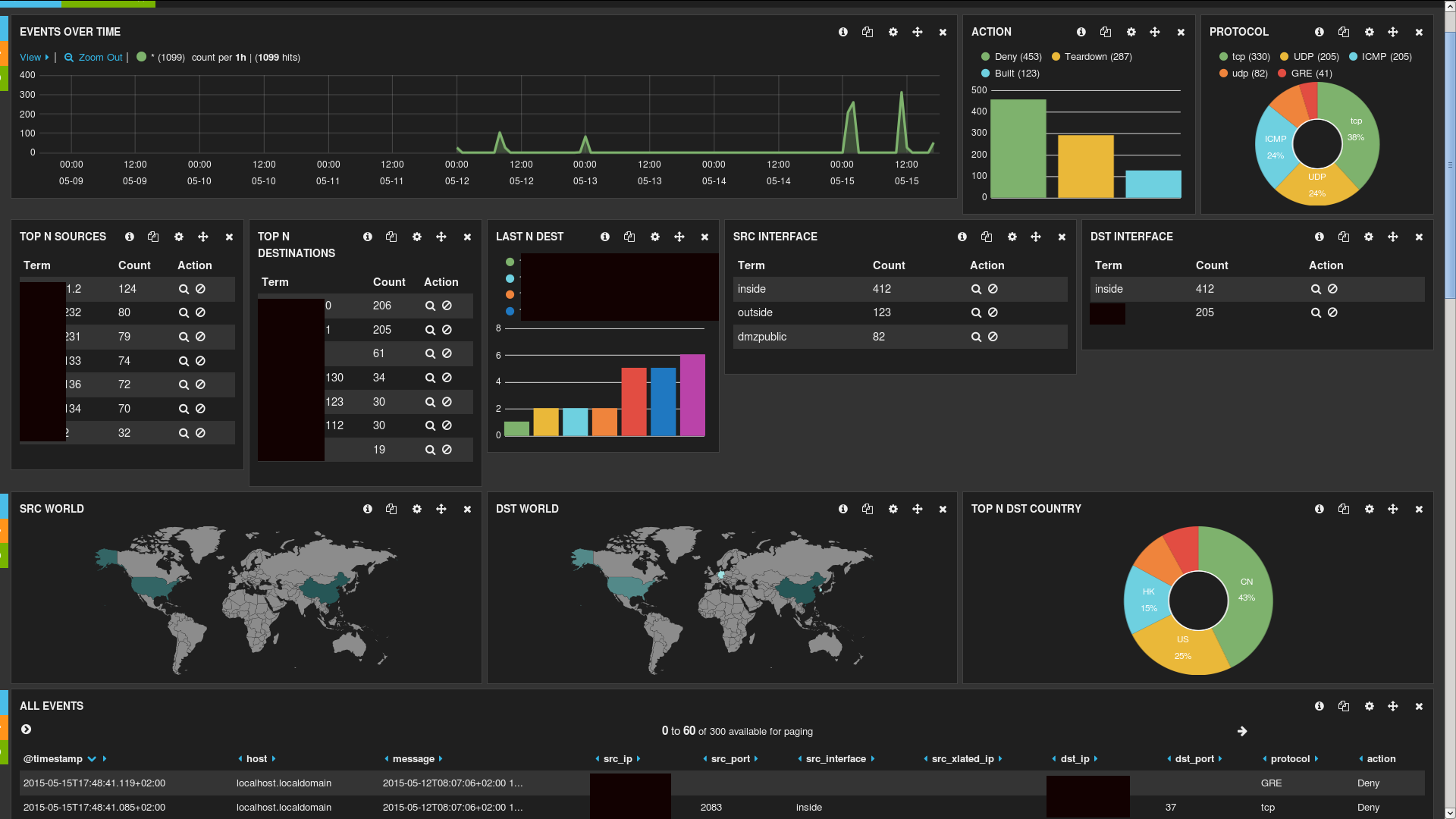
Setting Up Threat Intelligence
Integrate real-time threat intelligence into your SOC to proactively identify and mitigate threats. Our threat intelligence platform provides actionable insights to keep your organization safe from emerging threats.
- Real-time threat monitoring
- Integration with threat intelligence feeds
- Automated threat detection and response
- Visualizations and reports on threat landscape

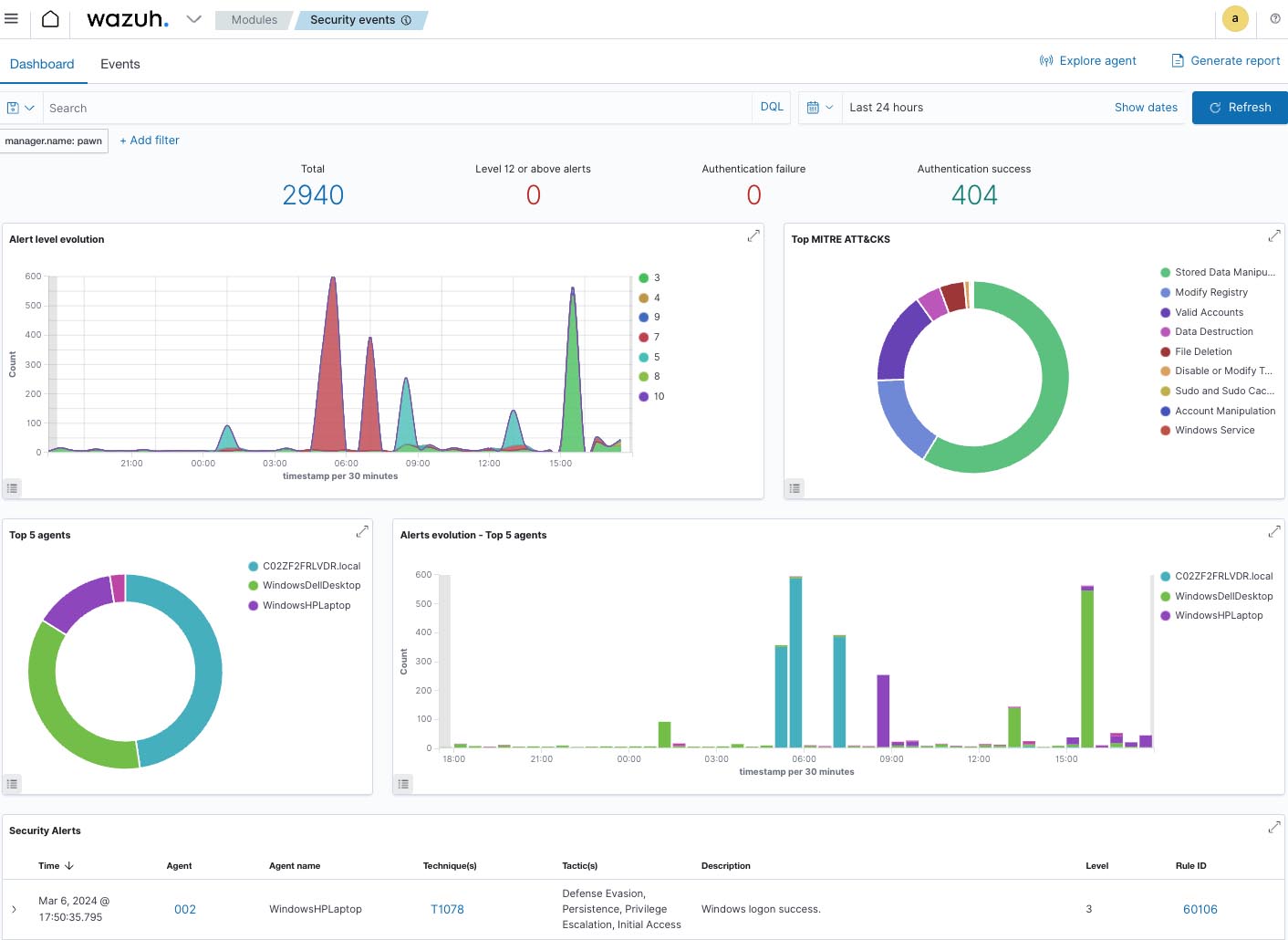
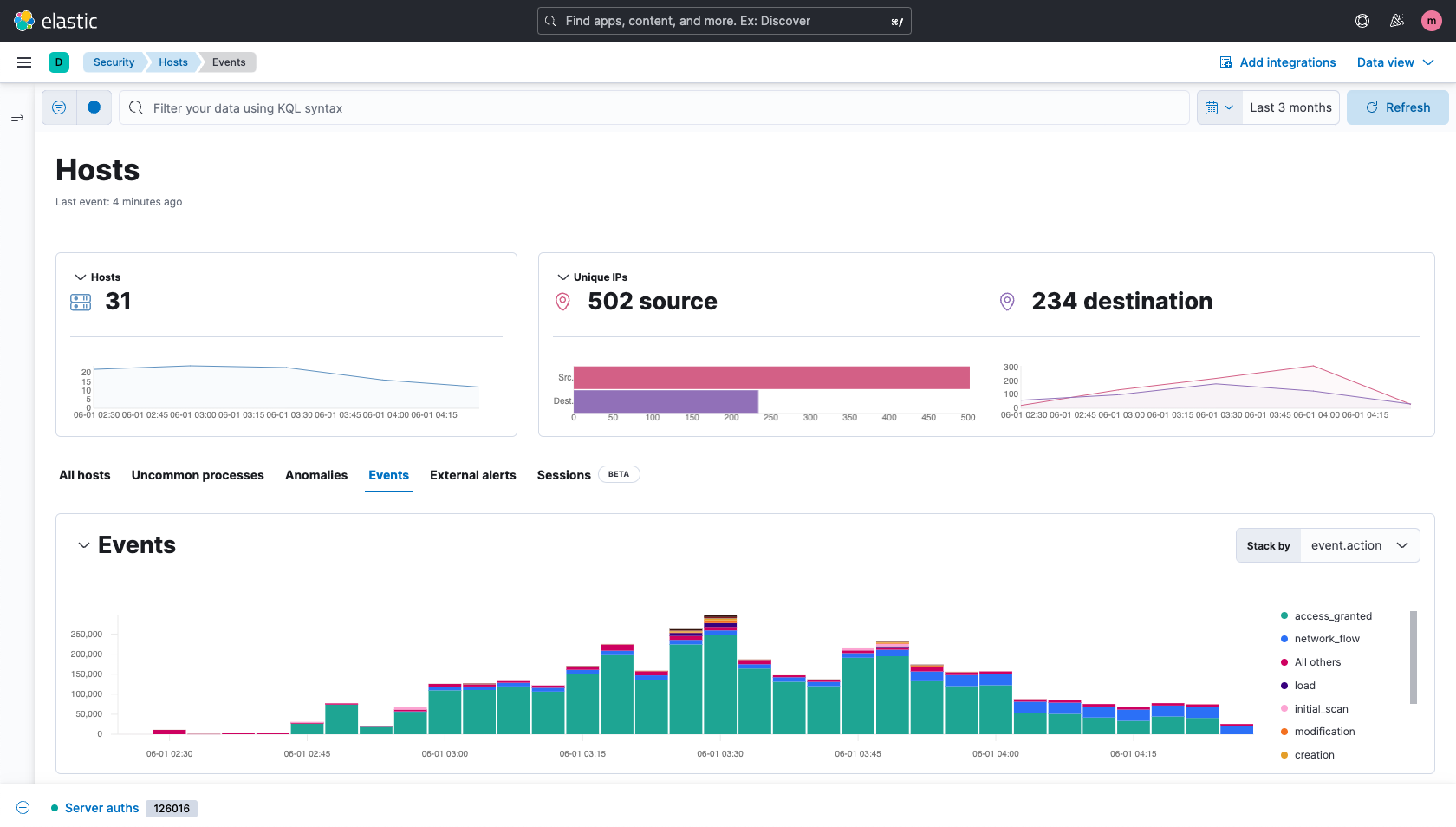
24/7 SOC Monitoring
Our SOC analysts provide round-the-clock monitoring to ensure your infrastructure is protected at all times. We use state-of-the-art tools and techniques to detect and respond to threats in real time.
Setting Up CSIRT
Establish a dedicated Cyber Security Incident Response Team (CSIRT) to manage and respond to security incidents effectively. Our experts help you build a robust CSIRT structure integrated with your SOC operations.
- Incident detection and analysis
- Incident response and recovery
- Post-incident review and improvement
- Coordination with external stakeholders
Setting Up Security Orchestration Platform
Enhance your SOC's efficiency with our security orchestration platform. Automate repetitive tasks and coordinate incident response actions across your security tools and systems.
- Automated incident response workflows
- Improved coordination between security tools
- Reduced response times
- Enhanced overall SOC efficiency

Setting Up In-House SOC
Our experts assist you in establishing a fully functional in-house SOC tailored to your organization's requirements. We provide end-to-end support from initial setup to ongoing management, ensuring your SOC is equipped to handle the latest threats.
- Complete control over security operations
- Customization to meet specific needs
- Integration with existing infrastructure
- Enhanced data privacy and control

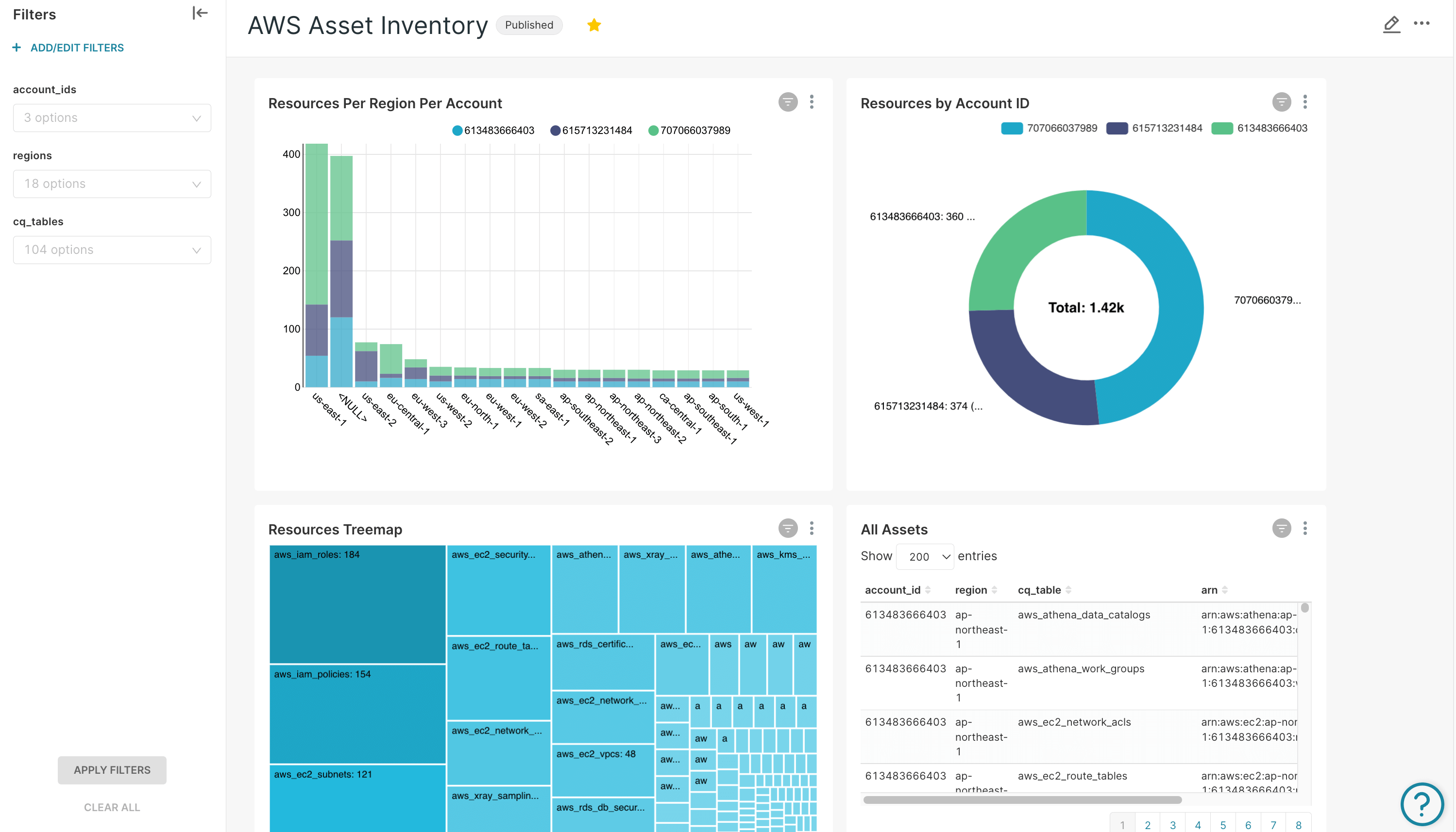
Log Source Integrations
Integrate over 500 log sources to ensure comprehensive monitoring and threat detection. We support integrations with Wazuh, WAF logs, CloudTrail Logs, CloudFlare Logs, Kubernetes Logs, Guard Duty, VPC Flow Logs, and more.
- Improved threat detection and response
- Comprehensive visibility across your infrastructure
- Enhanced forensic and investigative capabilities
- Seamless integration with existing tools and platforms
Training and Support
Empower your team with the knowledge and skills to effectively use the SOC. We provide comprehensive training programs and continuous support to ensure your SOC operates at peak efficiency.
- Introduction to SOC operations
- Incident detection and response
- Using dashboards and visualization tools
- Advanced threat detection techniques
Setting Up Incident Management
We help you set up a comprehensive incident management platform to streamline your response to security incidents. Our platform integrates with your SOC to provide a seamless workflow for detecting, analyzing, and responding to incidents.
- Centralized incident tracking and management
- Automated workflows for incident response
- Integration with threat intelligence feeds
- Customizable reporting and analytics
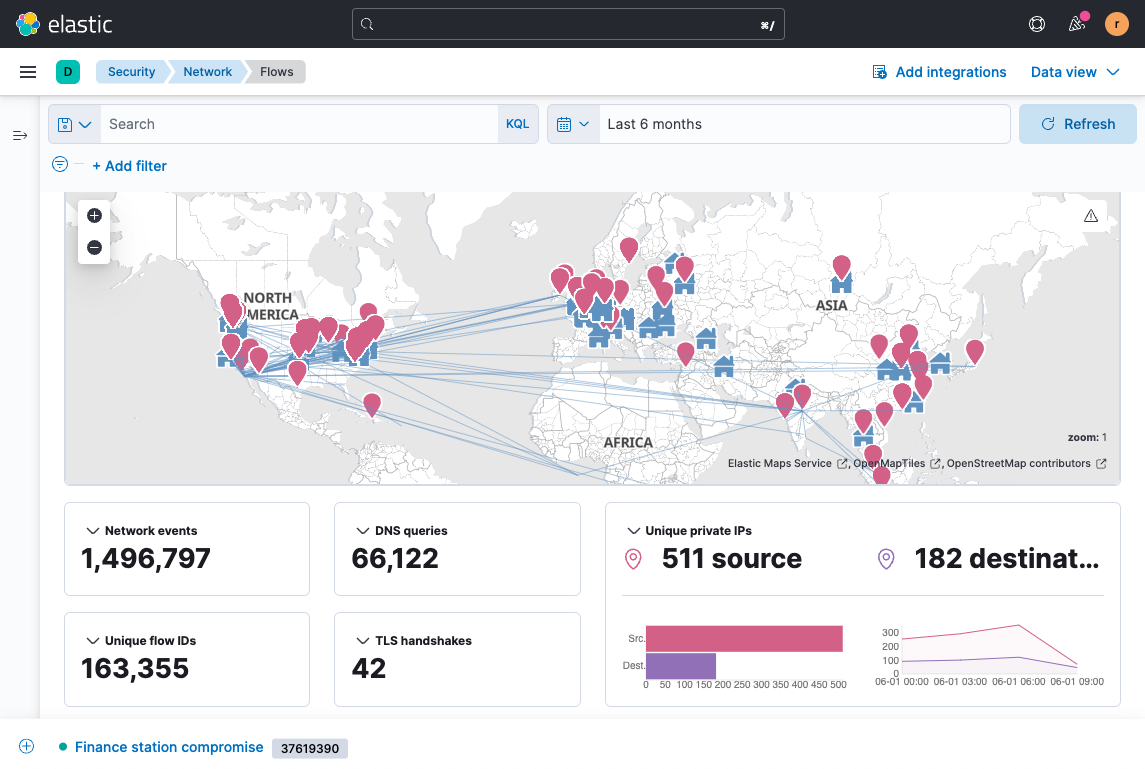
Real-Time Security Alerts
Set up real-time security alerts to respond to threats promptly. Customize alerting rules and choose from multiple alert destinations including Slack, JIRA, Hive, Email, Mattermost, PagerDuty, and more.