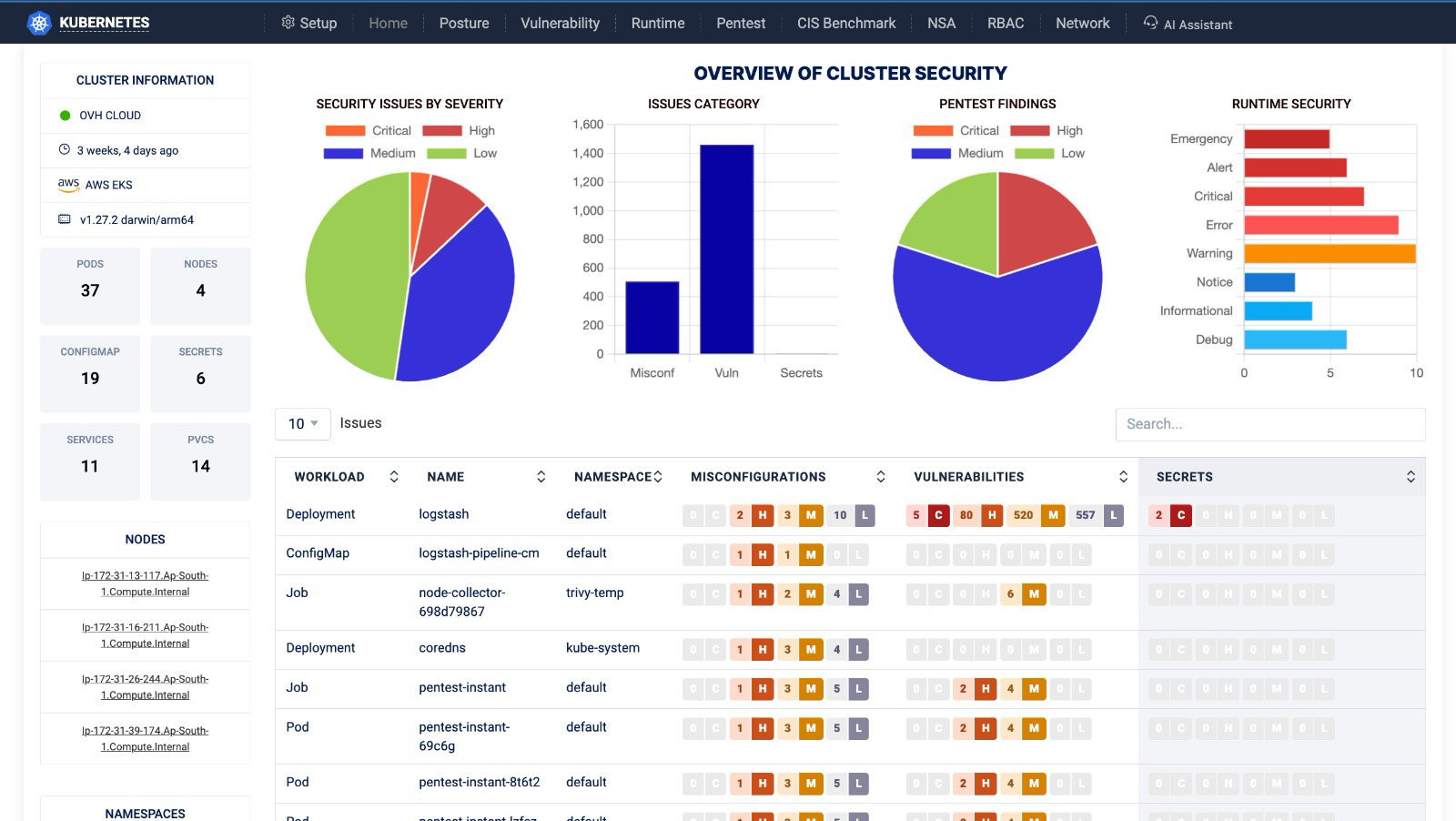
Kubernetes Security Posture Management (KSPM)
Ensure your Kubernetes configurations adhere to best practices and security standards. Our KSPM services continuously monitor and assess your Kubernetes environment to identify and remediate potential security risks.